How Do We Encrypt Your Data?
This is our detailed encryption method, using only industry-standard public algorithms, which means you can decrypt your data without LocalFileEncrypt.com, ensuring you always have complete control over your encrypted data (as long as you remember the key!)

- Bobby Li

The encryption process consists of three steps:
- Record metadata, which is used to record the original file type and necessary encryption operation metadata.
- Encrypt the original data using the AES-256-GCM algorithm.
- Combine metadata and encrypted data into a single file.
1. Recording Metadata
Metadata is a JSON object containing the following fields:
{
version: number;
type: "0" | "1" | "2";
ext?: string
}
Their meanings are as follows:
| Field Name | Data Type | Optional | Description |
|---|---|---|---|
| version | number | No | The LocalFileEncrypt.com version number that performed the encryption, used to identify the encryption process version, currently fixed at 1 |
| type | “0”, “1”, “2” | No | Target type for encryption, “0” represents text encryption; “1” represents file encryption; “2” represents folder encryption |
| ext | string | Yes | The extension of the encrypted file, only exists when type is “1” |
For example: When encrypting a foo.txt file, the metadata is:
{
"version": 1,
"type": "1",
"ext": "txt"
}
2. Encrypting Original Data
The process of encrypting original data is related to the version field in the metadata, which determines the specific encryption procedure.
When version is 1 (current version)
- Read the original file binary data stream as the original data.
- Use the SHA-256 algorithm to generate a 256-bit hash digest of the password, which serves as the IV.
- Use the PBKDF2 algorithm to convert the password into a base key, which is only used for key derivation.
- Use the PBKDF2 algorithm to derive a 256-bit encryption/decryption key from the base key, where the hash algorithm is SHA-256, iteration count is 100000, and the salt is the same as the password.
- Use the AES-GCM algorithm to encrypt the original data, where the iv is the 256-bit iv generated in step 2, and the key is the 256-bit key generated in step 4.
3. Combining Metadata and Encrypted Data
The combination process uses the following steps:
- Convert the JSON metadata into a string format.
- Create a binary buffer.
- Sequentially write 8 bytes to the buffer, with the content ’l0kfd3e1’, indicating that this is a LocalFileEncrypt.com encrypted file, this value is constant.
- Sequentially write 4 bytes to the buffer, with the content being the length of the metadata string, in big-endian order.
- Sequentially write the metadata string content to the buffer.
- Append all encrypted data to the buffer.
For example, when encrypting text with the content ‘123’ and the password ‘123’, the final data in hexadecimal representation is:
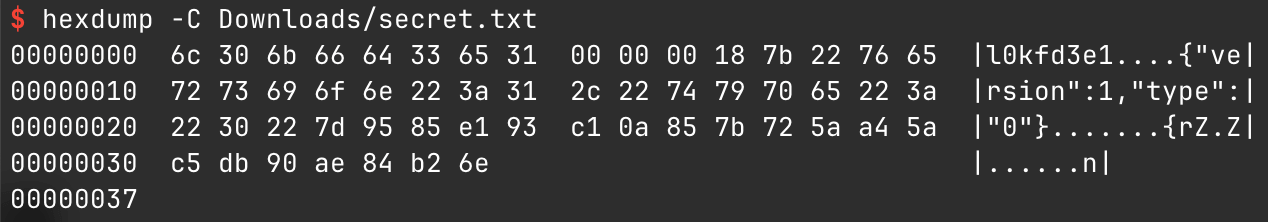
4. Decrypting Without LocalFileEncrypt.com
Under normal circumstances, you don’t need to worry about being unable to decrypt data encrypted by LocalFileEncrypt.com. We rely on Cloudflare to provide highly available services globally.
However, you may still want to decrypt data locally without LocalFileEncrypt.com to ensure complete control over your encrypted data. For this purpose, we provide a Python example program that implements data decryption based on the encryption process described earlier. You can decrypt data locally using the following method:
python3 decrypt.py <file_path> <key>
*Note: This example program is for reference only. You can modify it according to your needs. Before executing, please ensure that Python and cryptography are installed.
5. Update Log
- 2025/01/31: Added encryption process for version 1
LocalFileEncrypt.com is constantly evolving, and different encryption algorithms and key sources may be added in the future. All process details will be disclosed here to ensure that your encrypted data can always be decrypted as long as you have the key, regardless of any force majeure.
- Tags:
- How We Work