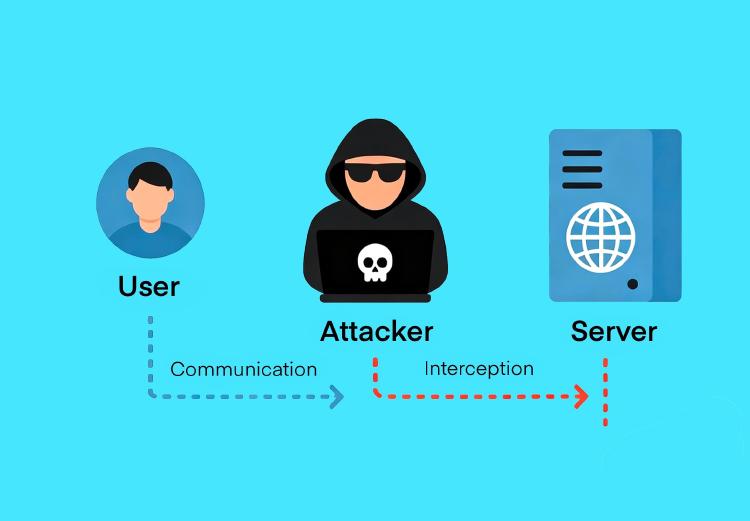
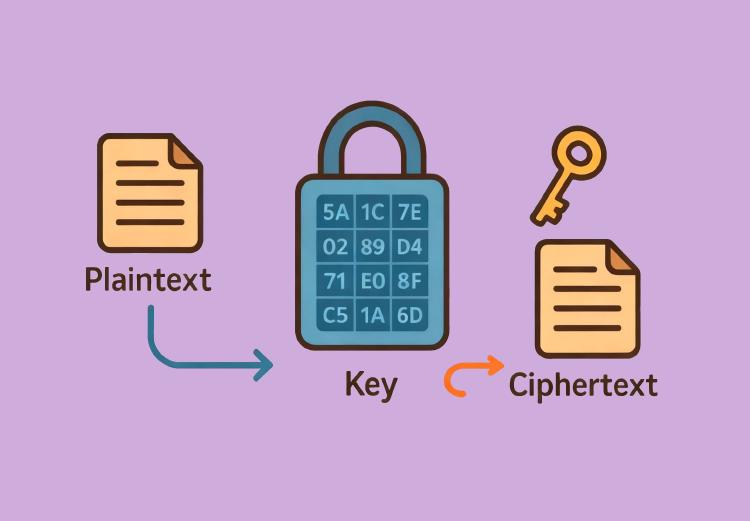
How Do We Encrypt Your Data?
This is our detailed encryption method, using only industry-standard public algorithms, which means you can decrypt your data without LocalFileEncrypt.com, ensuring you always have complete control over your encrypted data (as long as you remember the key!)