How Do MITM Attacks Steal Your Data?
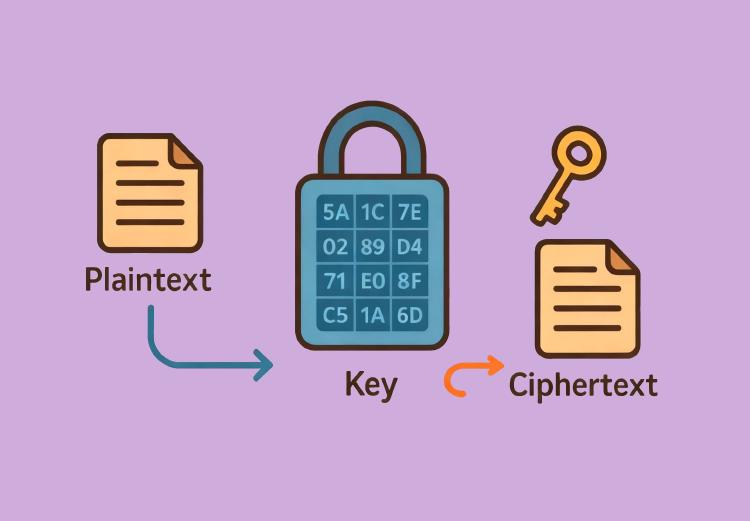
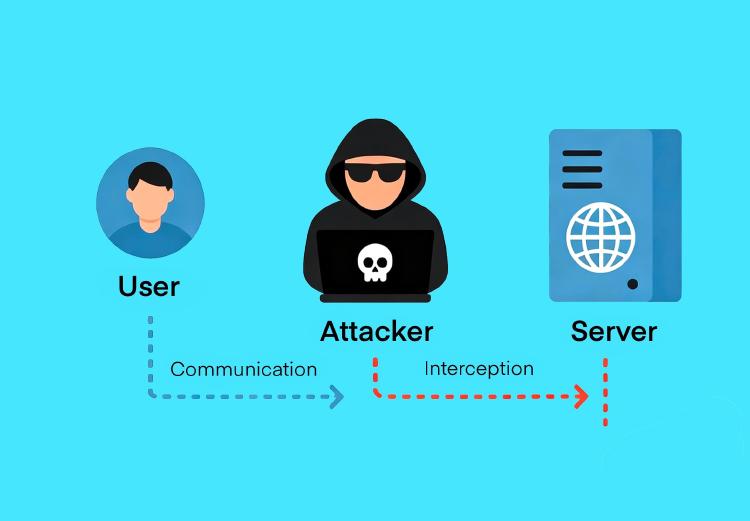
A Man-in-the-Middle (MITM) attack is a stealthy network attack method where an attacker inserts themselves between two communicating parties to steal or alter data. This article explores the principles, threats, and defensive measures of MITM attacks.